What is Wazuh
Objective
To install the open source security tool called Wazuh see how it can be used to keep a host secure.
Background
Wazuh is a host-based intrusion detection and prevention system. It runs on your computer and monitors it - who's coming in and who's going out. If anything suspicious happens, it can notify the administrator and sometimes, take actions to keep the system from being taken over.
One of the most common suspicious activity is a brute force login. This is where an attacker just tries to login to your computer using every password combination that can be tried. Another suspicious activity could be a sudden increase in the number of processes that are dialling out a specific server - your computer could now be part of of Denial Of Service attack - by overloading the remote server. Wazuh can detect this, and many other suspicious activities.

A truly safe computer is one that is not connected to the power outlet. Every other computer can be a target.
Prerequisites
- Access to a cloud account (DigitalOcean is used here, but substitute instructions for the cloud of your choice)
Steps
You will need to create two VMs - one runs the wazuh-server and the other acts as the client running the wazuh-agent. You can create droplets in digital ocean to create these VMs. Follow the official documentation at https://documentation.wazuh.com/current/getting-started/index.html. Jump to the quick-start installation here. Pay close attention to the minimum requirements wrt VM resources.
- The server runs just fine with 4GB RAM.
- The client runs fine with 2GB RAM.
In a real world scenario, you might need more juice. But for a test setup, this much is fine.
First, create the wazuh-server. Once it is up, setup the wazuh-agent on a client VM. While installing the wazuh-agent you should provide the IP address of the wazuh-server, so that the former can register itself with the server.
Test
Step 1: Scan for suspicious events
- Open
https://<server-ip. To change the default password (displayed during the installation) see this link.
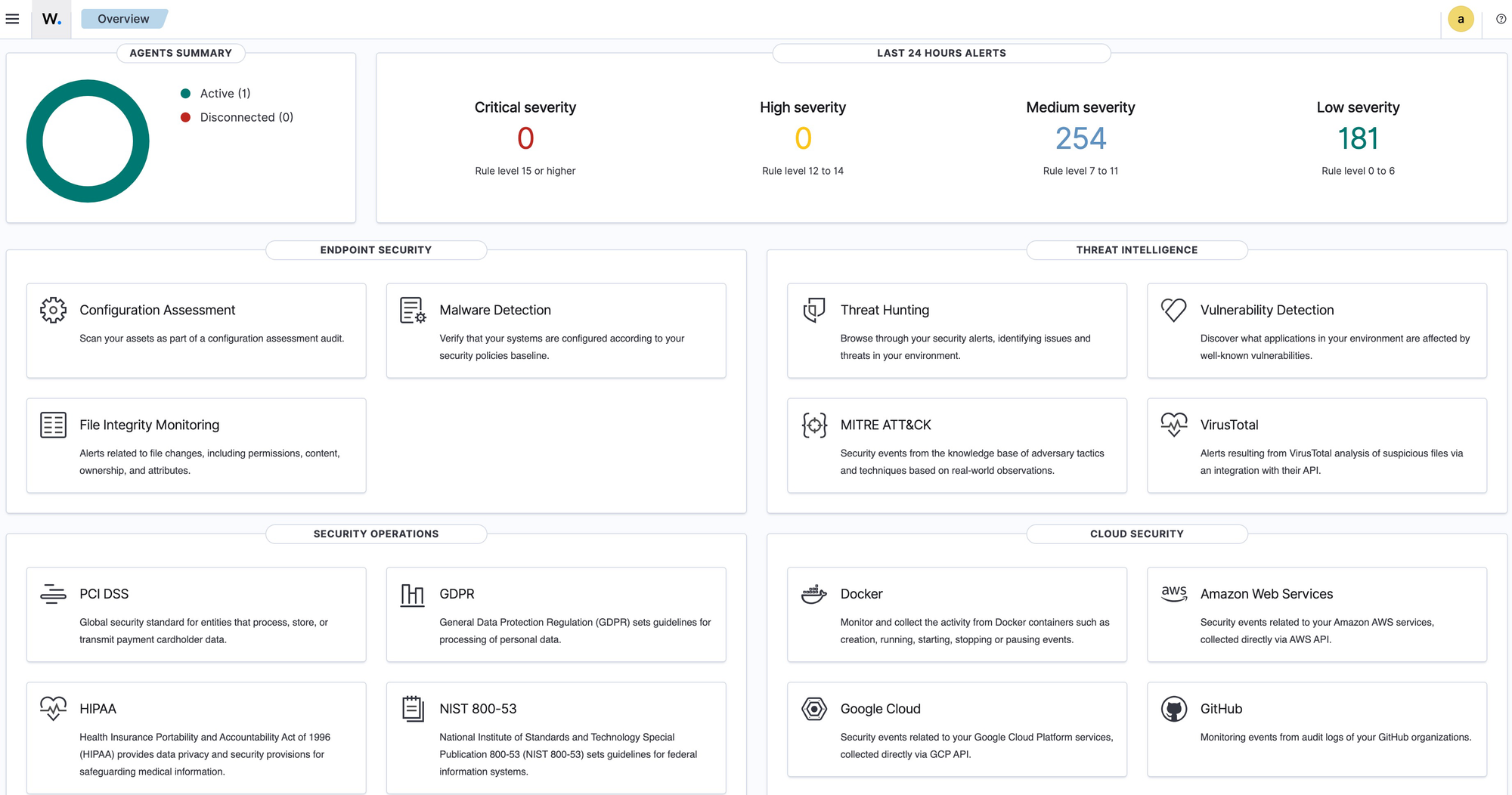
- Click on 'Threat Hunting' within the Threat Intelligence section.
- The threat hunting homepage is displayed.

- There are 256 authentication failure events on this server. That seems suspicious. In the next step we will drill down into these events. Click on 'Events' tab.
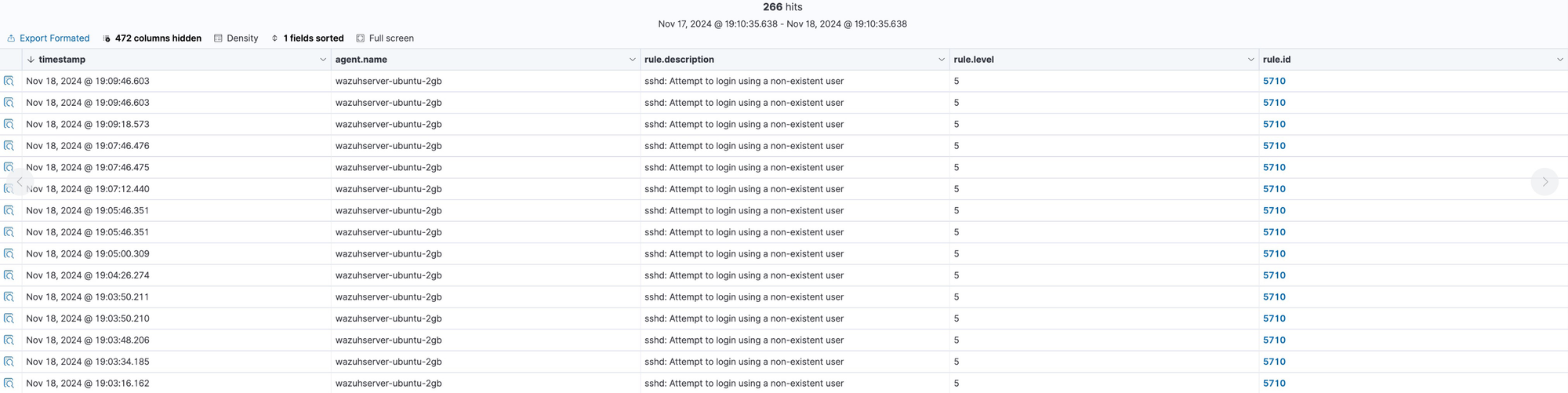
- Timestamps are now seen for all the times that the attacker has tried to login. Click on the lens icon at the left for one of the records.
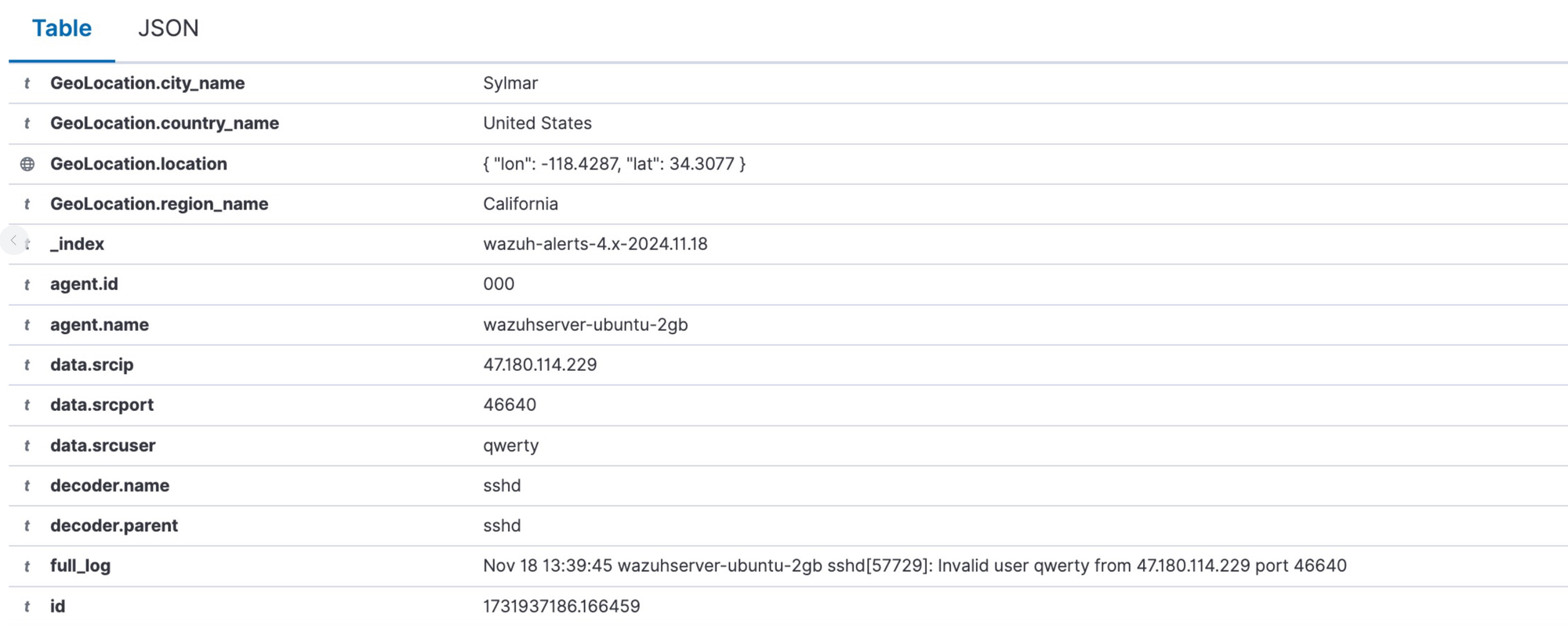
- The hacker has been trying to login using
qwerty@<server-ip>. Of course the attempt failed as there is no such user, but it was worth a shot. The hacker (most likely a bot) will continue trying many common usernames to try and get in.

- As you can see here, there is also an oscar, dolphinscheduler, dev, deploy, demo and many other attempts.
Step 2: Scan for mis-configurations
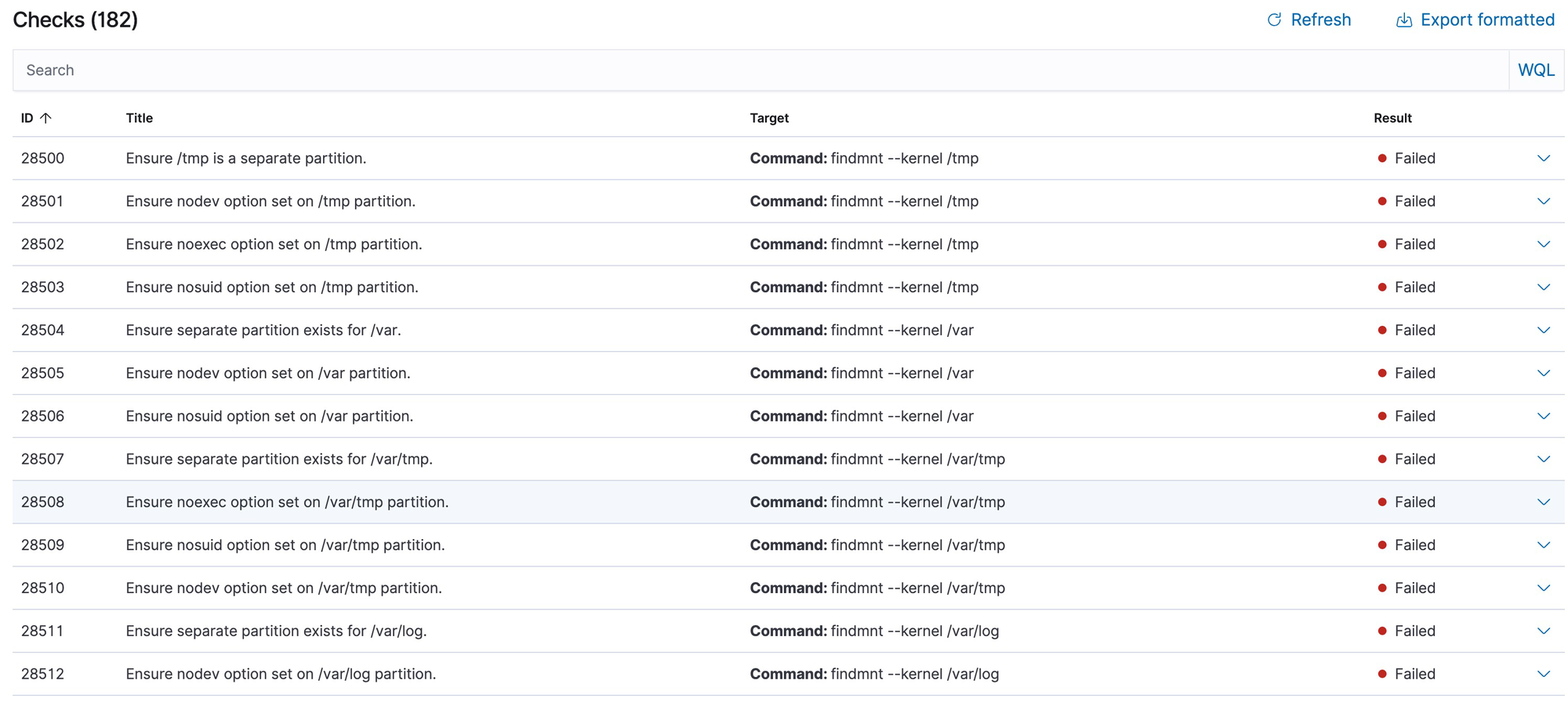
The wazuh-agent running on the client scans the configuration of the host machine and provides a report. This is like a blood report - you pass some, and you fail some. Pay attention to the failures. Standard configuration checks exist for many different OS distros. Here is one that does not seem to be doing particularly well.
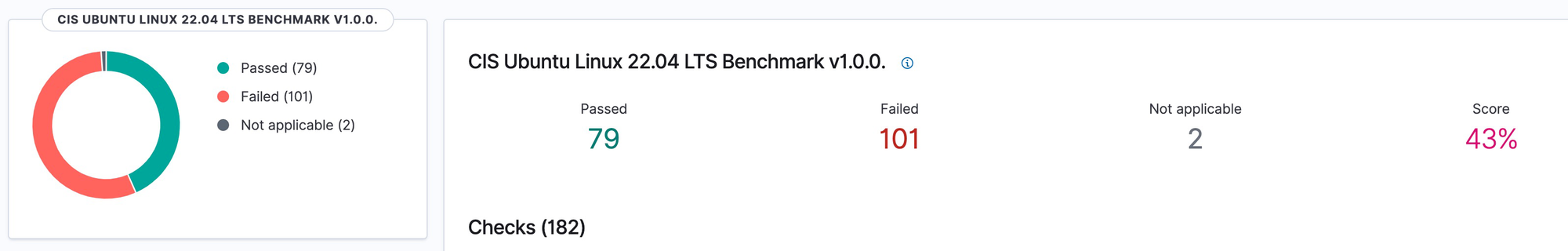
A partial listing of some of the items that failed the 'secure configuration posture' check.
The configuration assessment feature is based on the SCAP framework - a framework used for automating the assessment, measurement, and management of security compliance in systems. SCAP defines a set of standards that allow security configurations to be automatically verified against established benchmarks, reducing the manual effort involved in compliance and ensuring more consistent and effective security posture assessments. Vulnerabilities, when found, are described using OVAL (Open Vulnerability and Assessment Language).
SCAP plays an important role in compliance. For example in the case of PCI-DSS compliance, SCAP can be used to assess whether a system is correctly configured to protect payment card information, including ensuring encryption settings, user authentication configurations, and firewall rules.
Wazuh uses OpenSCAP tool for the configuration assessment. Here are some sca logs emitted:
Step 3: Scan for vulnerabilities
The wazuh-agent runs a vulnerability scan and automatically reports the information to the wazuh-server.
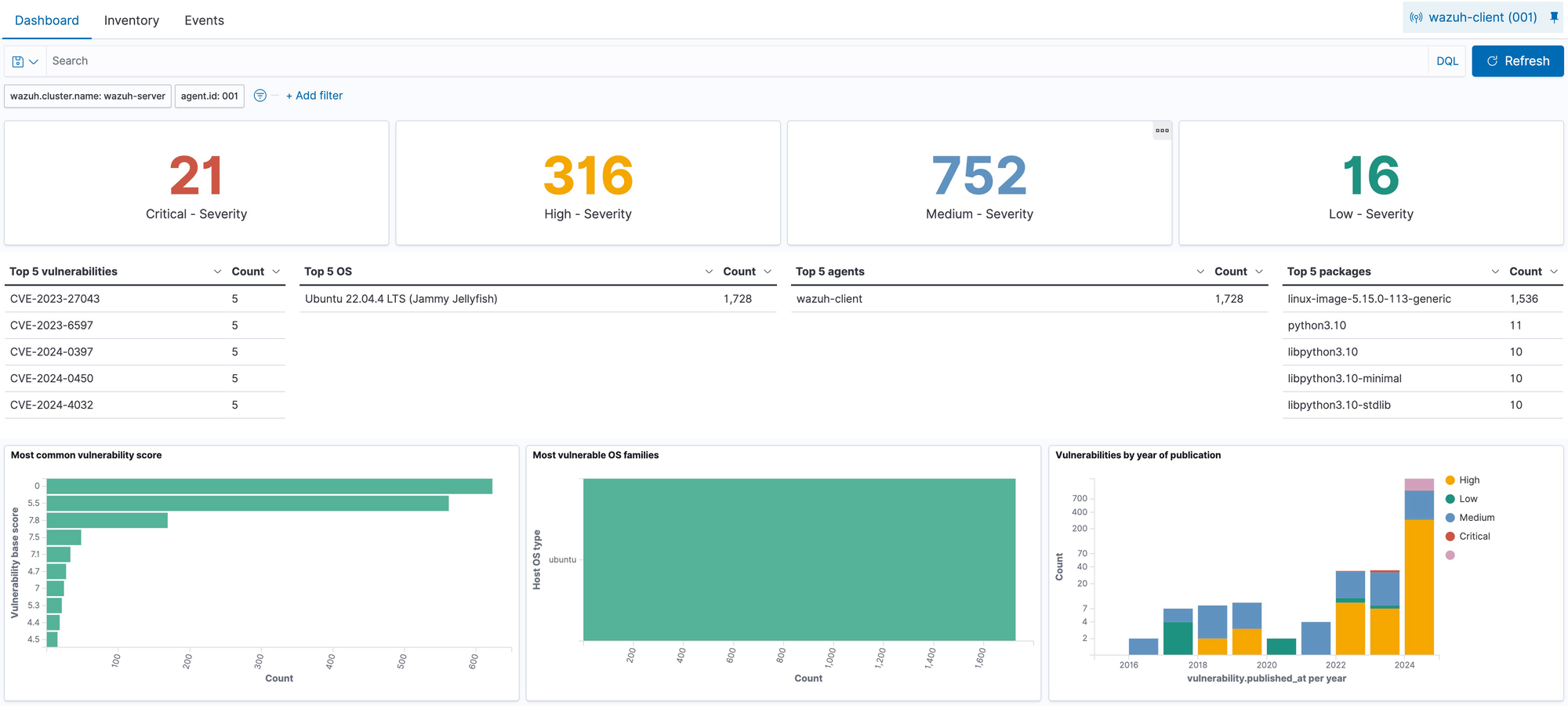
Click through a vulnerability and read it's description.
CVE-2024-8088: There is a HIGH severity vulnerability affecting the CPython "zipfile" module affecting "zipfile.Path". Note that the more common API "zipfile.ZipFile" class is unaffected. When iterating over names of entries in a zip archive (for example, methods of "zipfile.Path" like "namelist()", "iterdir()", etc) the process can be put into an infinite loop with a maliciously crafted zip archive. This defect applies when reading only metadata or extracting the contents of the zip archive. Programs that are not handling user-controlled zip archives are not affected.
Note the "Vulnerabilities by year of publication." The older a vulnerability, the more likely there is a patch out there that addresses the issue.
Vulnerability assessment and configuration assessment have the same goal - to let you know the attack surface a malicious user has at his disposal. But the attack surfaces are completely different.
Dig Deeper
- Go through each panel and try to simulate an attack in order to populate data into the panel.
